How to deploy AppLocker with Microsoft Intune? In an era defined by evolving cyber threats, securing your organization’s digital environment is paramount. Enter AppLocker, Microsoft’s robust application control solution, now made even more accessible and efficient when paired with the management prowess of Microsoft Intune. In this blog post, we’ll guide you through the process of How to deploy AppLocker with Microsoft Intune, empowering you to fortify your organization’s security posture and shield against potential threats.
Table of Contents
What is AppLocker?
AppLocker is a security feature in Microsoft Windows that lets administrators control which applications and scripts can run on a system. It enhances security by creating rules that specify allowed executables, installers, and scripts, reducing the risk of unauthorized or malicious software execution.
Policy Creation: Administrators create rules that define which applications are allowed or denied. These rules can be based on attributes like the application’s path, publisher, or file hash. For instance, a rule can allow all applications signed by a specific publisher or only those located in certain directories.
Rule Types: AppLocker supports different types of rules for various file categories:
- Executable rules: Control .exe and .com files.
- Windows Installer rules: Control .msi and .msp files.
- Script rules: Control scripts like .ps1, .bat, .cmd, .vbs, and .js files.
- Packaged app rules: Control Universal Windows Platform (UWP) apps.
- DLL rules
What are we going to set up?
In this blog post we are going to show you How to deploy AppLocker with Microsoft Intune. In the first Step we will show you the process of defining default and custom rules. If you already have your AppLocker rules defined you can skip this step. In the second step we are going to export the AppLocker rules. In the last step we will import the AppLocker rules to Microsoft Intune and deploy it to a device.
- Step 1: Create an AppLocker Policy – In this step we are going to create the AppLocker Policy with the help of the Local Group Policy Editor. If you already have a AppLocker Configuration you can skip this part.
- Step 2: Export AppLocker rules – In this step we are going to export the AppLocker rules from step 1 into a XML file.
- Step 3: Import AppLocker rules and deploy with Intune – In this section we are going to import and deploy the AppLocker rules with Microsoft Intune.
- Optional: Consider AppLocker Hardening Rules – We will show you some optional things how you can harden your AppLocker configuration.
How to deploy AppLocker with Microsoft Intune

Create an AppLocker Policy
In the first step we are going to create the AppLocker rules. We can create AppLocker rules for the following file types:
- Executable files: .exe and .com
- Windows Installer files: .msi, mst, and .msp
- Scripts: .ps1, .bat, .cmd, .vbs, and .js
- DLLs: .dll and .ocx
- Packaged apps and packaged app installers: .appx and .msix.
Enable AppLocker policy
For this tutorial I will only configure the Executable files. To create the AppLocker rules we are going to use the local Application Control Policies in the local GPO settings. Please use a test machine or a virtual machine to create the rules. Trust me, i experienced some ugly situation when create the AppLocker rules on my own device :). We first need to activate the AppLocker service. Follow this steps:
- Connect to a test machine. In my case I will use a virtual machine.
- Press Windows + R to open Run Dialog box
- Type secpol.msc and press Enter
- Expand Application Control Policies
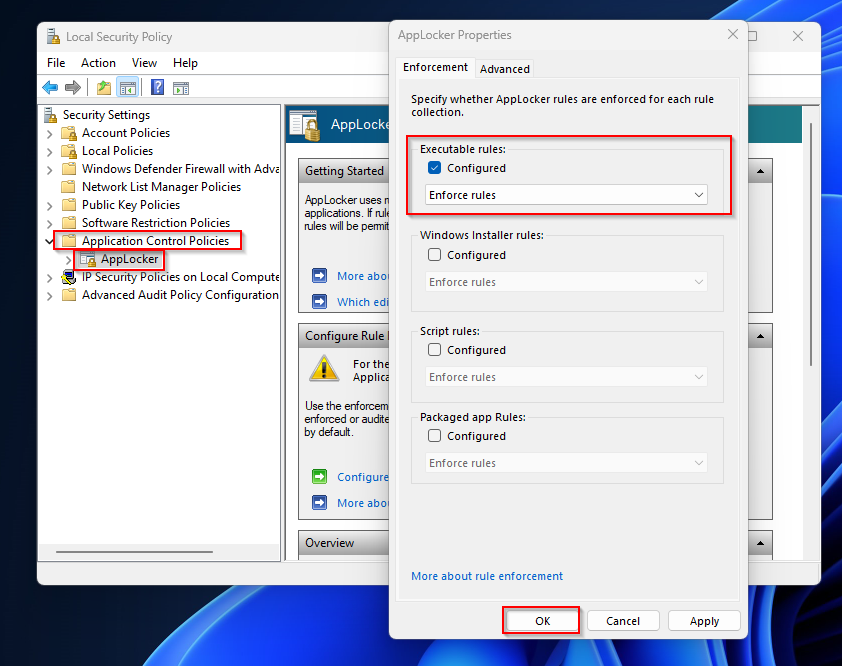
- Right-click AppLocker and select Properties
- Check Configured box under Executable rules section and select Enforce rules from the drop-down menu. If you want to also configure the other file types you can also enable those. For this blog post I will only configure the Executable files.
- Click on OK
We have now enabled the AppLocker policy and can start creating the rules.
Add AppLocker default rules
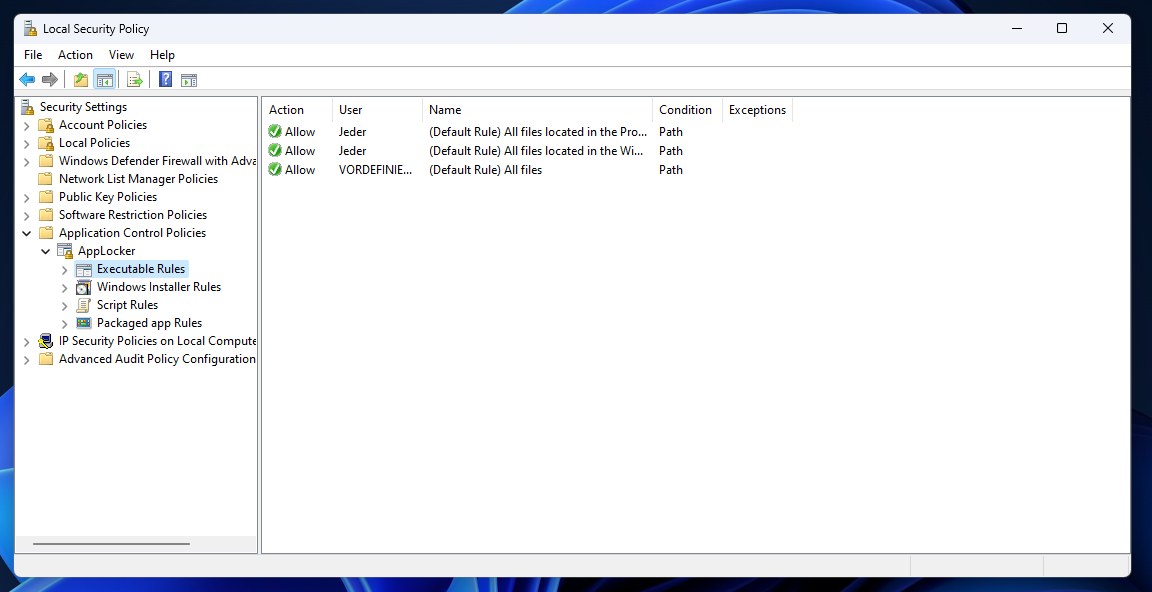
First of all I recommend adding the default rules. These rules are essential that Windows and affected programs still can run normally. It will make sure that executables from C:\Program Files and C:\ Windows folder can run. In addition a third default Allow rule is created for Administrator as per default, Administrator can execute All files from any location and are not restricted by the AppLocker policy.
- Press Windows + R to open Run Dialog box.
- Type secpol.msc and Press Enter
- Expand Application Control Policies
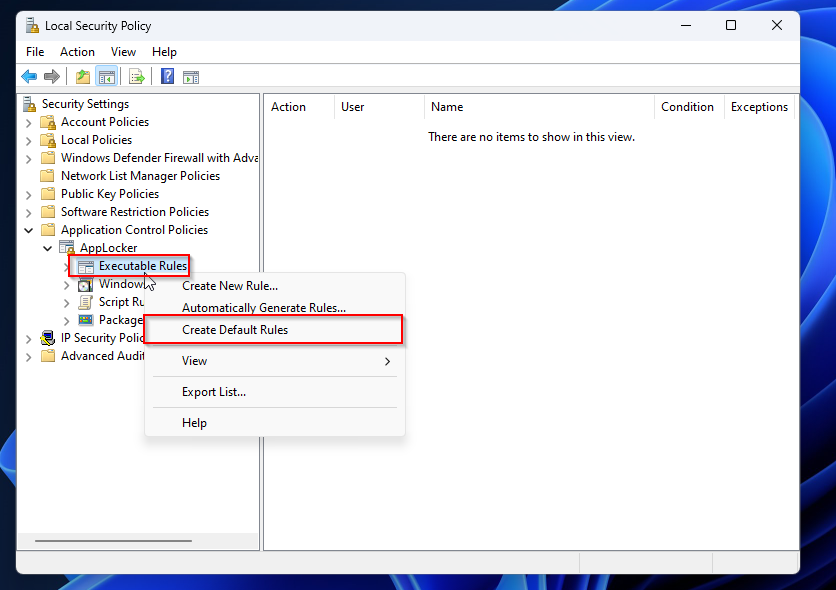
- Expand AppLocker
- Right-click on Executable Rules and click on Create Default Rules.
Create Custom AppLocker rules
We can now create custom AppLocker rules to deny specific applications from executing on the device. In most environments we want to deny the following applications: CMD, PowerShell and Registry. I will show you, how you can deny CMD for example.
- Press Windows + R to open Run Dialog box.
- Type secpol.msc and Press Enter
- Expand Application Control Policies
- Expand AppLocker
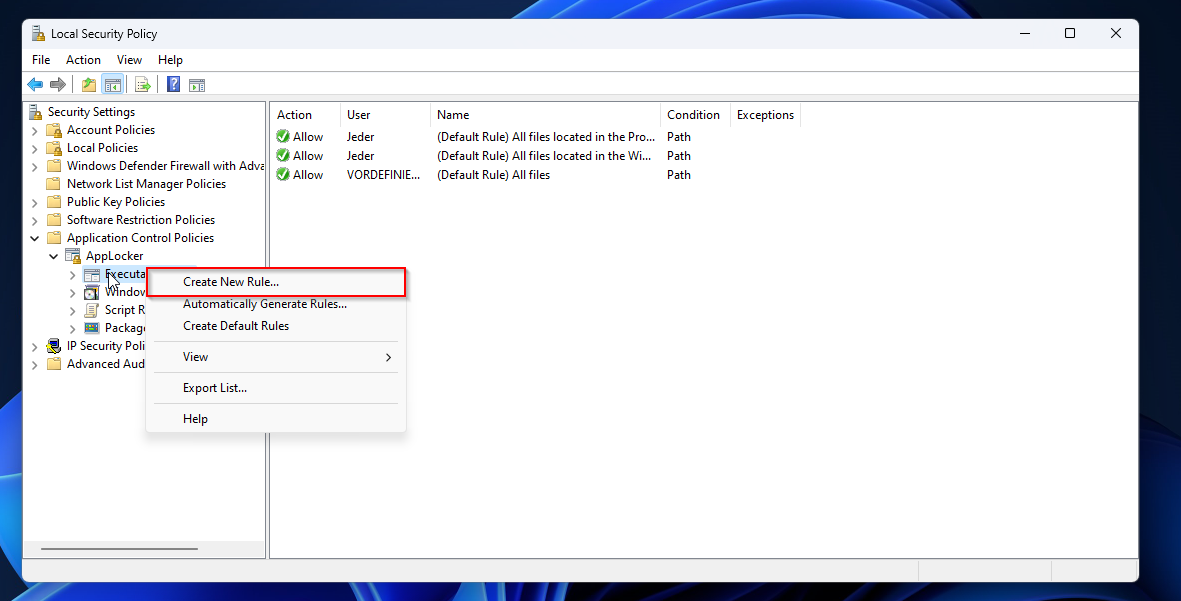
- Right-click on Executable Rules and click on Create New Rule
A new windows will open.
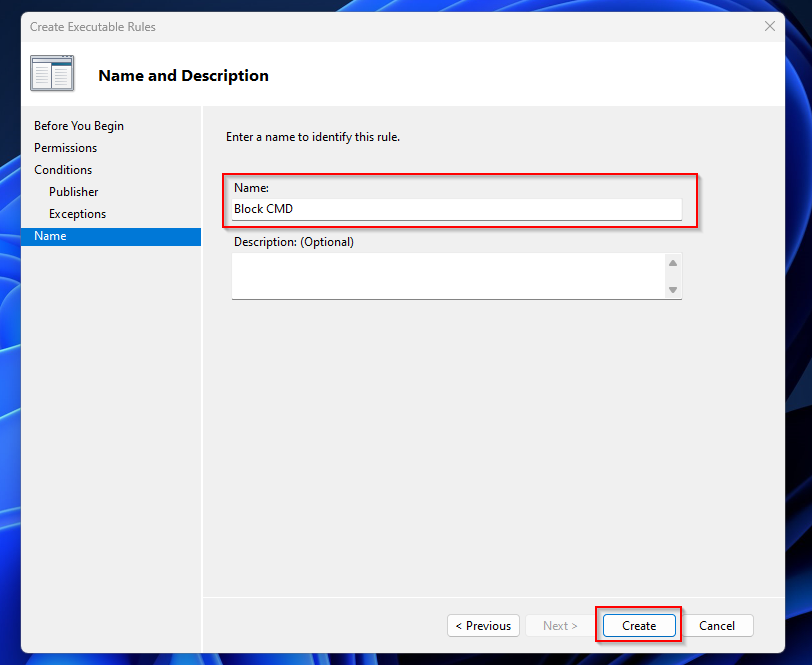
- Click on Next
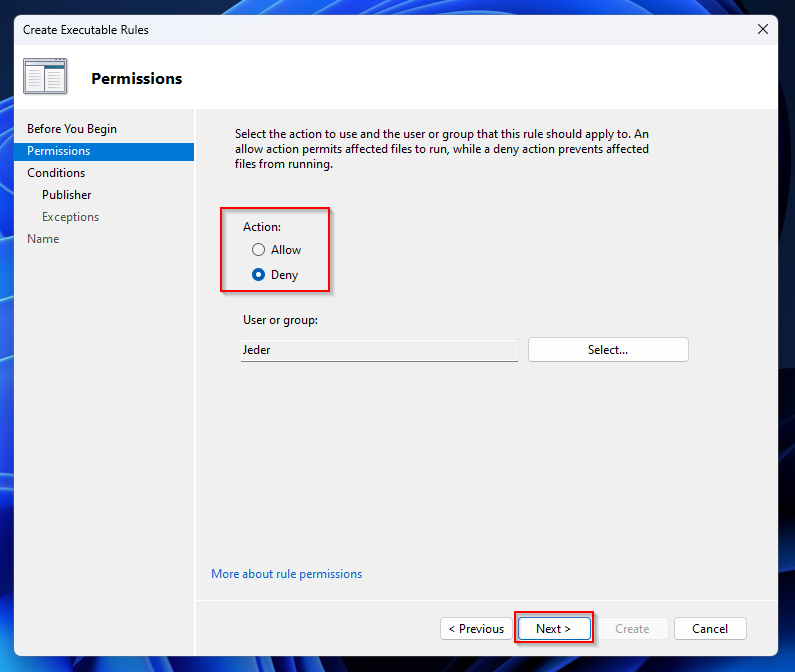
- On the Permissions tab choose Deny as Action. Click on Next.
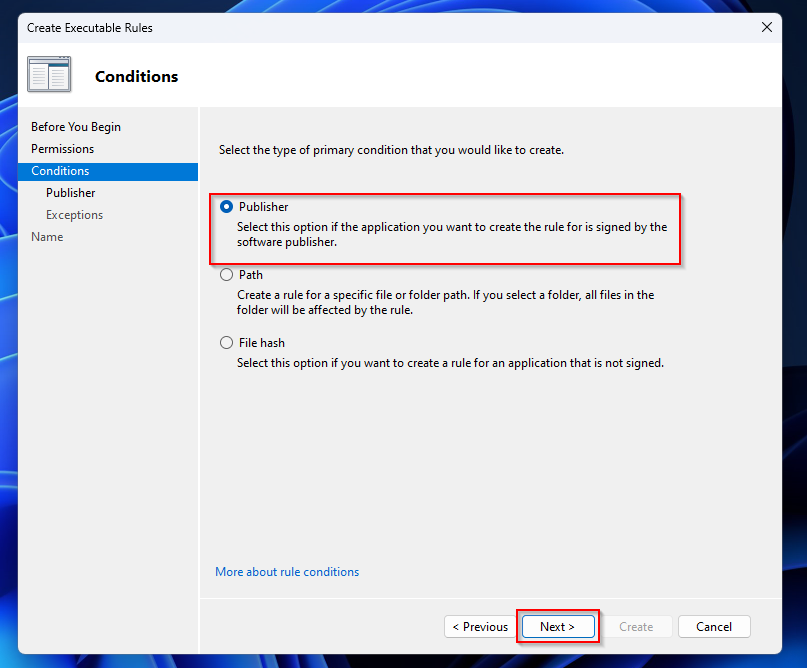
- On the Conditions tab choose Publisher. Click on Next.
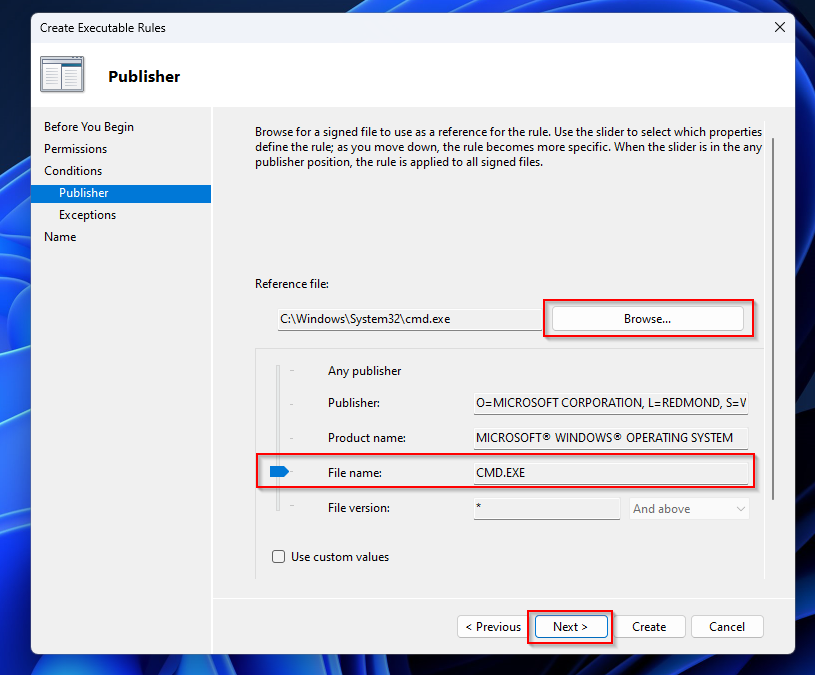
- Browse for the executable which you want to deny. I will browse for the CMD.exe.
- Make sure you deny the File name.
- Click on Next
- On the Exceptions tab you can add some Exceptions if applicable.
- Click Next
- Give it a meaningful name and click on Create

Export AppLocker rules
If we have created our AppLocker rules on our testmachine, we can go ahead and export the configuration. We need this XML file for the Intune policy in step 3. Follow this steps on the testmachine:
- Press Windows + R to open Run Dialog box.
- Type secpol.msc and Press Enter
- Expand Application Control Policies
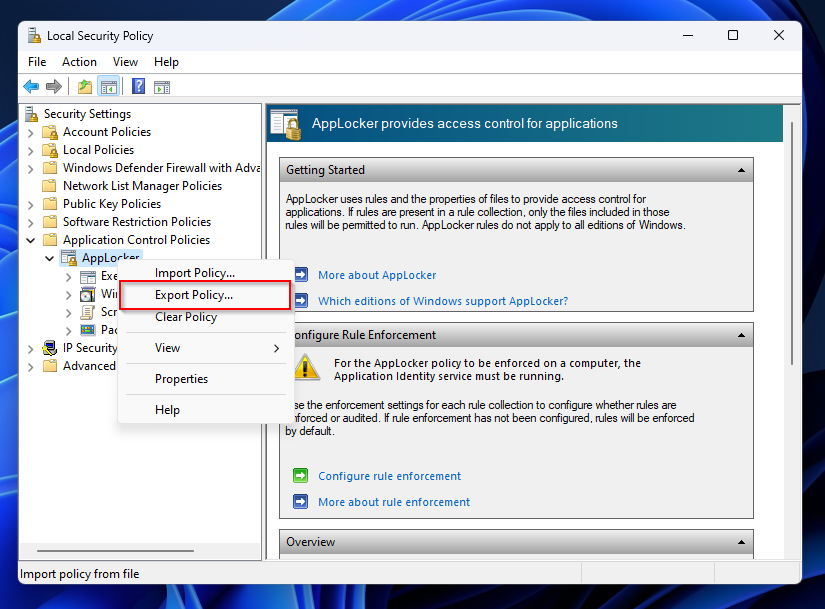
- Right Click on AppLocker and select Export Policy
- Save Applocker XML configuration file.

Import AppLocker rules and deploy with Intune
In this step we are going to create a configuraiton profile in Intune and import the XML file from step 2.
- Go to intune.microsoft.com
- Click on Devices
- Click on Windows
- Click on Configuration profiles
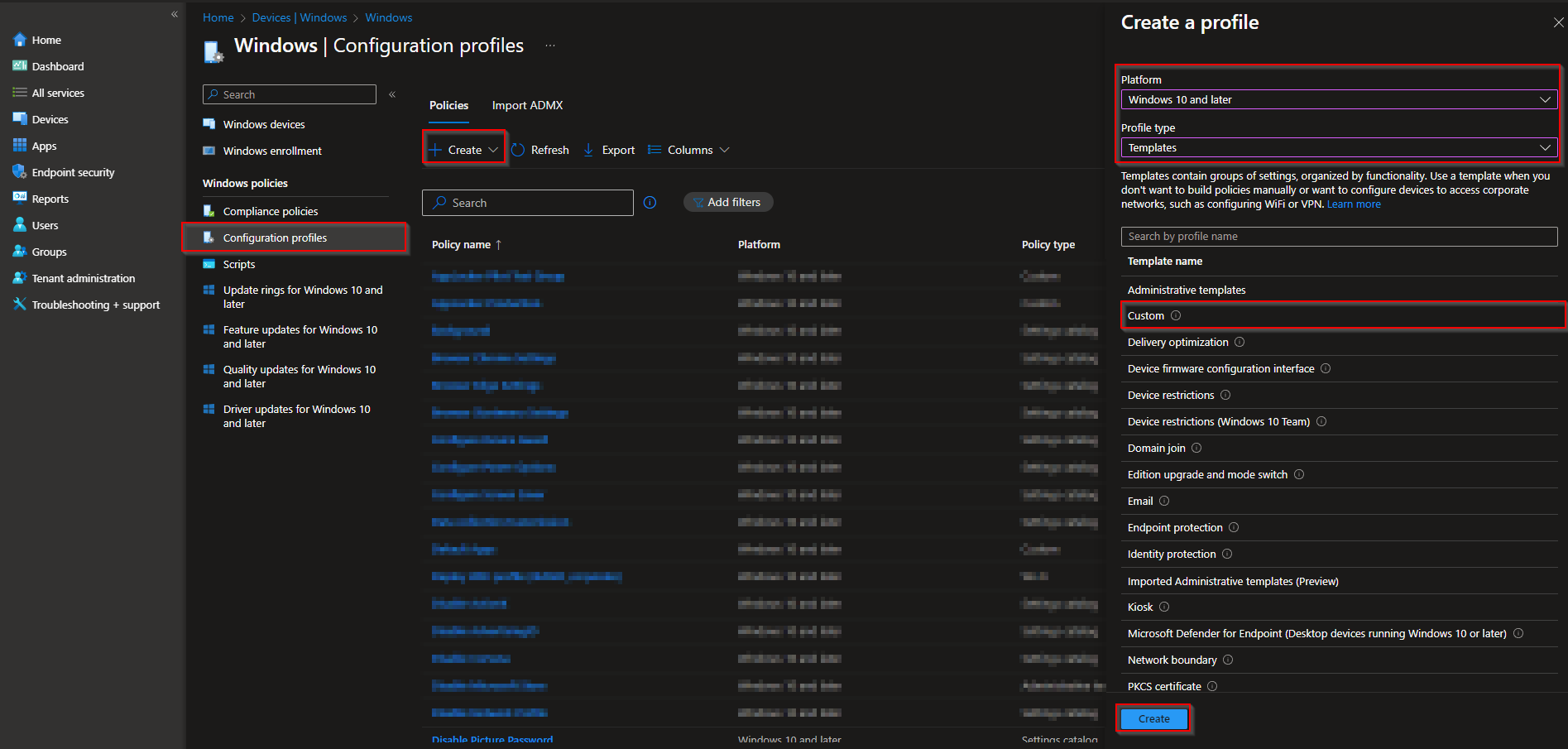
- Click on Create and Create new policy
- Select the Platform and set the Profile type to Templates
- Click on Custom
- Click on Create
- Give a Name and Description (optional) to the profile.
- Click on Next
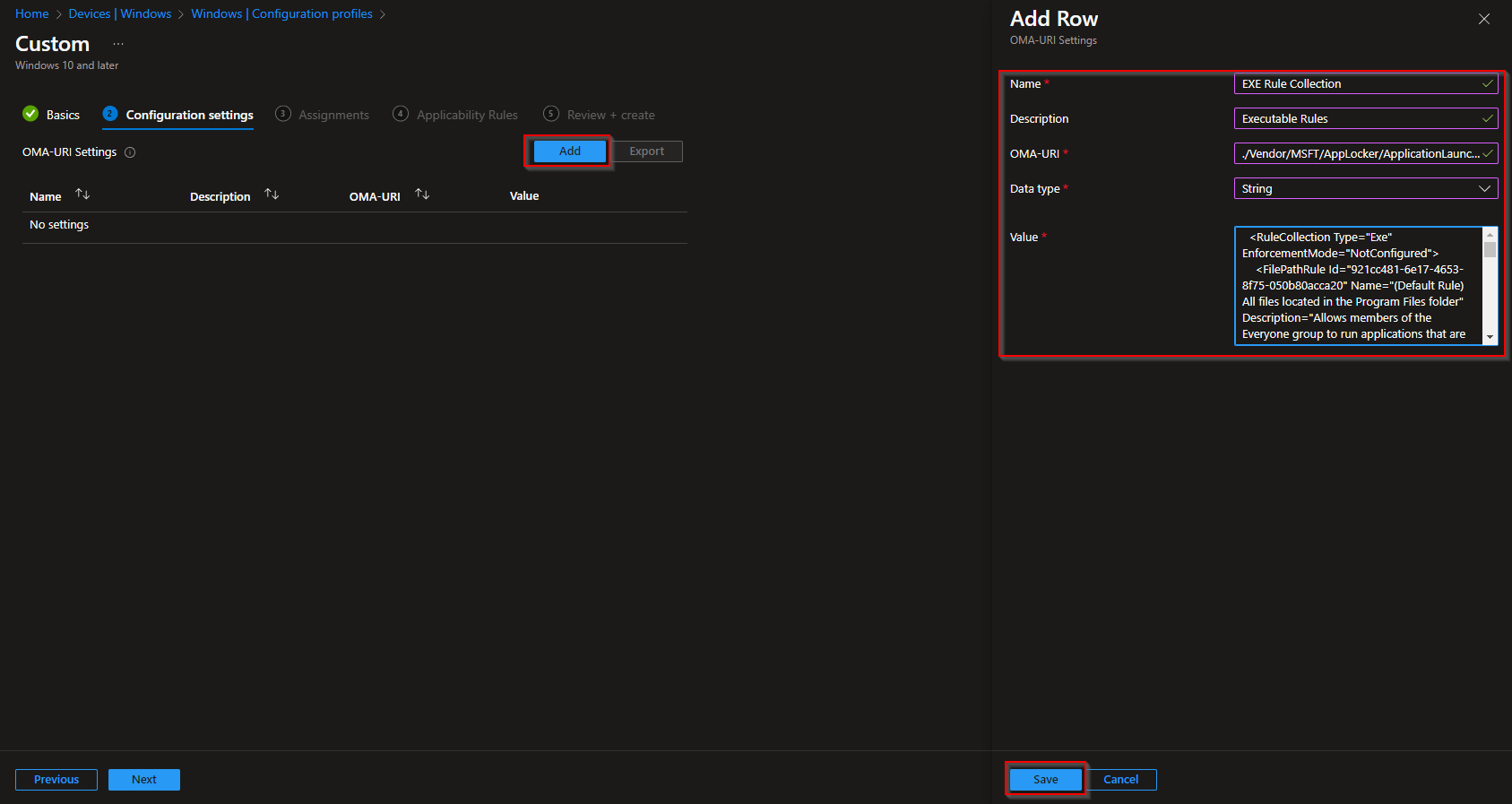
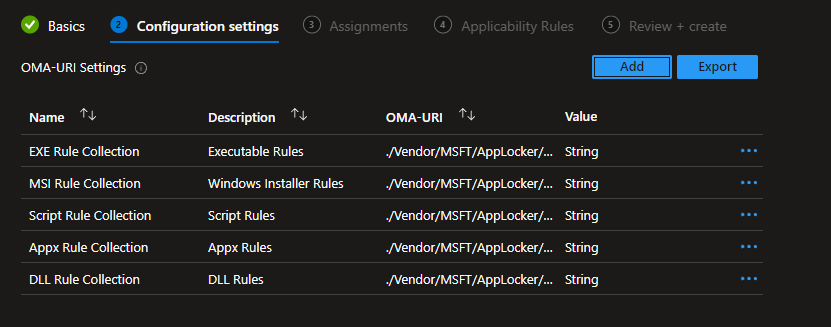
- Click on Add and add below OMA-URI setting:
- Name: EXE Rule Collection (You can provide whatever name you like)
- Description: Executable Rules
- OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/EXE/Policy
- Data type: String
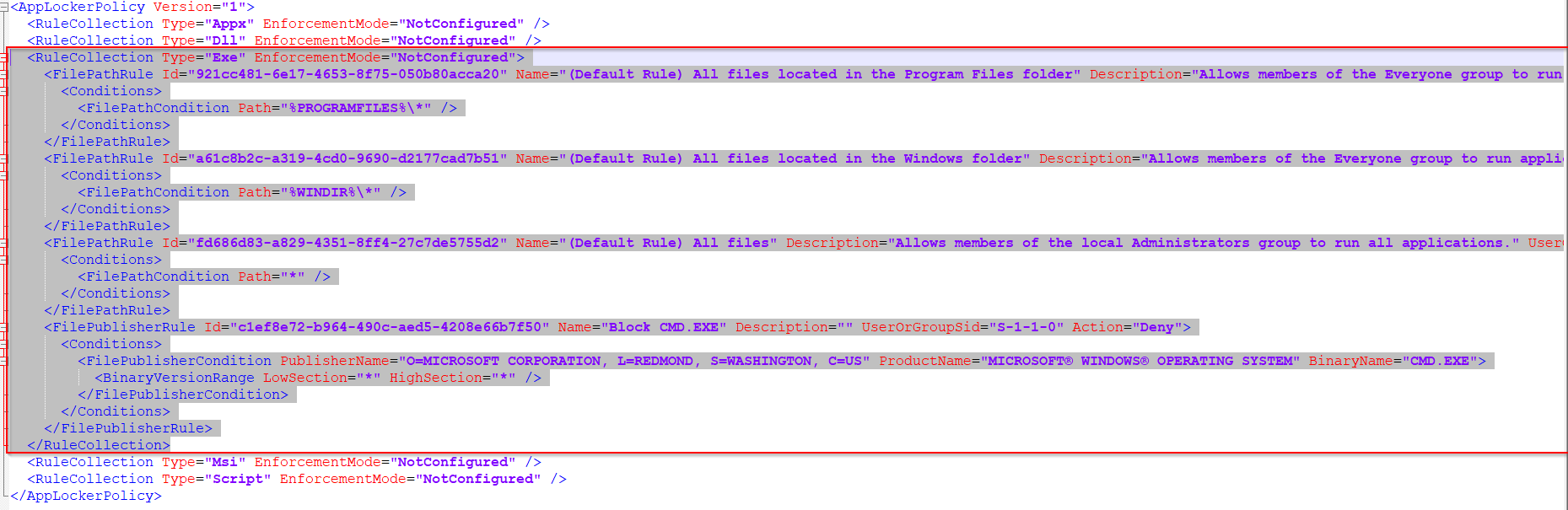
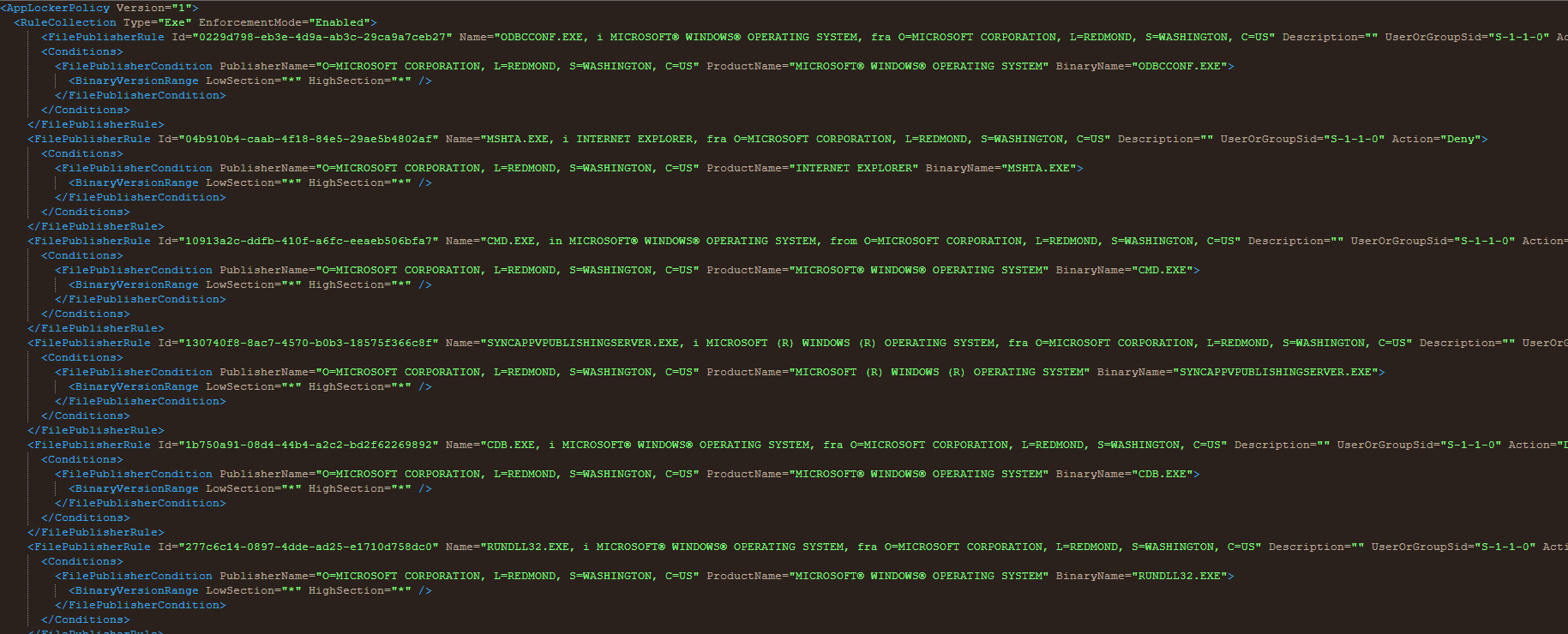
- Value: Copy and Paste XML file content from <RuleCollection Type> to </RuleConnection>
Important: Only copy the content between RuleCollection. Do not copy the AppLockerPolicy Version=1 from the beginning.
If you want to create othe AppLocker policies for the other file types, just use the OMA-URI settings from below.
- MSI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/MSI/Policy
- Script: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/Script/Policy
- Appx: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/StoreApps/Policy
- DLL: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/DLL/Policy
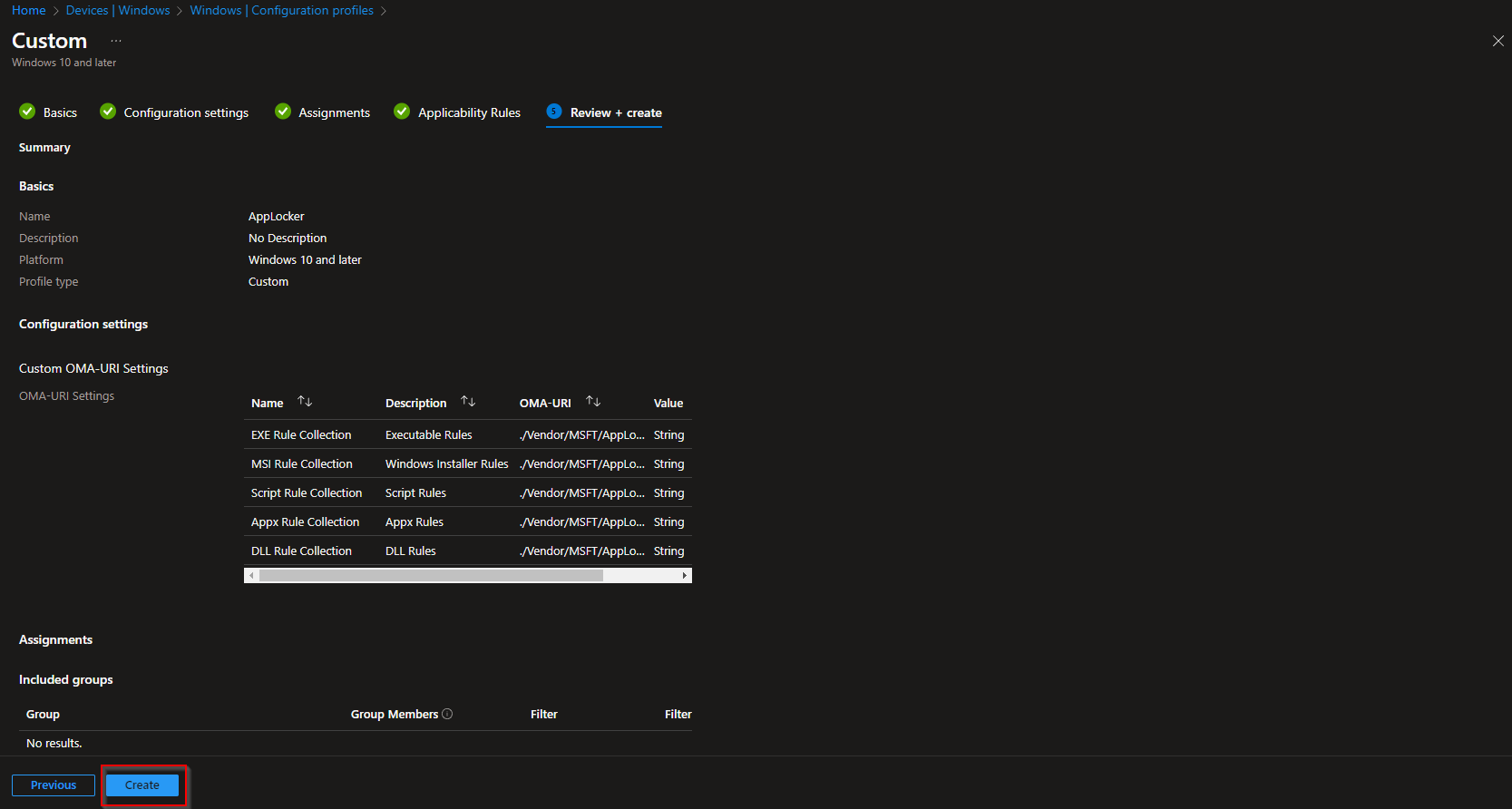
- Click on Save and Next.
- Scope tags, click Next
- Assignments – Select an Azure AD group containing devices or you can add all devices or all users. Click Next.
- Applicability Rules, click Next
- Review and Create, click Create

Consider AppLocker Hardening Rules
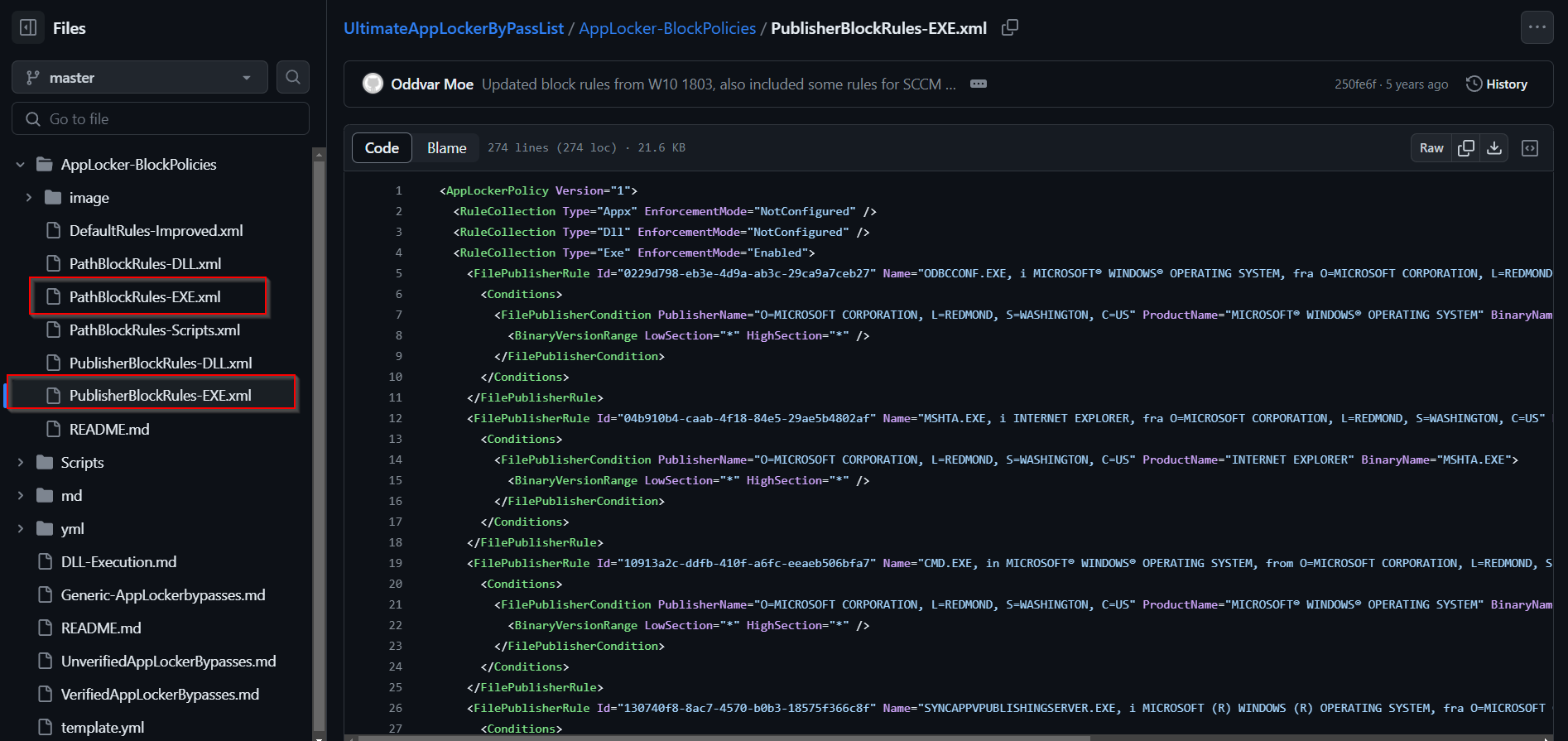
With the default AppLocker configuration its pretty easy to bypass the configuration. This can be done with placing files in writeable paths. If you want to learn more you can check Generic-AppLockerbypasses, VerifiedAppLockerBypasses and UnverifiedAppLockerBypasses. To harden your environment we will need some extra AppLocker rules. There is a good Github page from api0cradle where he created a collection of rules. Go check it out: https://github.com/api0cradle/UltimateAppLockerByPassList
The rules are already in XML fileformat which can be importet into AppLocker configuration.
Conclusion
You learned how to add AppLocker default rules and add a custom rule. We than exported the rules to an XML file. In the last step we created a configuration profile and imported the XML file. Did you enjoy this article? Dont forget to follow us and share this article.
Frequently asked questions
Where are the rules stored on the End User device?
The AppLocker rules are stored on the target device at: C:\Windows\System32\AppLocker\MDM
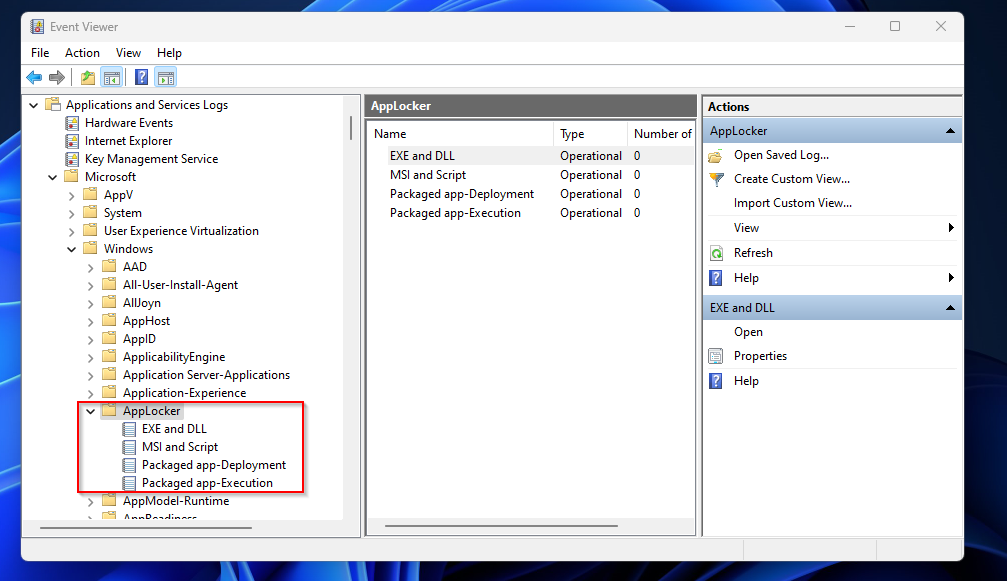
Where can I see AppLocker events in the Event Viewer?
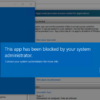
In the Event Viewer > Applications and Services Logs > Microsoft > Windows > AppLocker you can view al events from AppLocker. It will show for example which application were blocked. This helpes troubleshooting when something on the system isnt working.
Where are AppLocker rules stored in the registry?
You can locate AppLocker rules at below registry location:
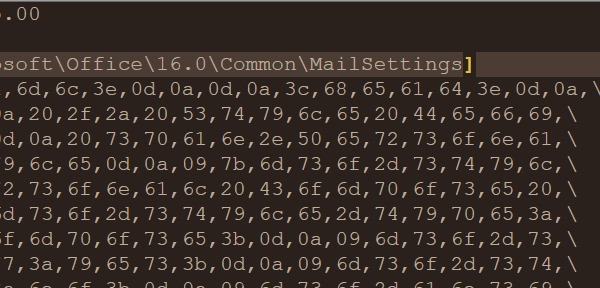
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SrpV2HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\SrpV2










app locker and intune natively allows execution of exe ( specific application installation with out administrator rights) both are same or different
how about the removal of the policy? is it a case of just removing the configuration profile from the device?
Hi unknownelf321
You can just remove the policy of the device. Applocker will then be removed from the device.
Kind regards
Max