In this blog post we will show you How to enroll existing Entra joined Devices to Microsoft Intune. More and more companies are switching to the Entra ID identity manager. In connection with this, Microsoft Intune is often used as MDM and MAM. We have often found that devices can be Entra ID Joined, but are not yet Microsoft Intune enrolled. This can happen, for example, if Microsoft Intune has not yet been configured as Automatic enrollment.
Here, for example, we have a device that is Entra ID joined but not yet enrolled in Microsoft Intune.
Unfortunately, there is no simple process from Microsoft for such cases on how to easily unroll them in Microsoft Intune. We will show you a few options here on how you can easily trigger the enrollment.
Option 1: In the first option we will trigger the enrollment using a PowerShell script. This method is extremely useful if you have installed an external RMM tool with which you can roll out PowerShell scripts. Of course, scripts can also be executed manually.
Option 2: In the second option, we will trigger the enrollment using the Sysinternal tool. This method is ideal for manual execution and not too many devices.
Table of Contents
Prerequisite
It is important that the execution on the devices must be done with administrator rights. Otherwise errors may occur. Furthermore, the users must be properly licensed for Intune, and the MDM scope should be open to the users or preferably for all.
Triggering the Enrollment
Option 1: Trigger the Enrollment with PowerShell script
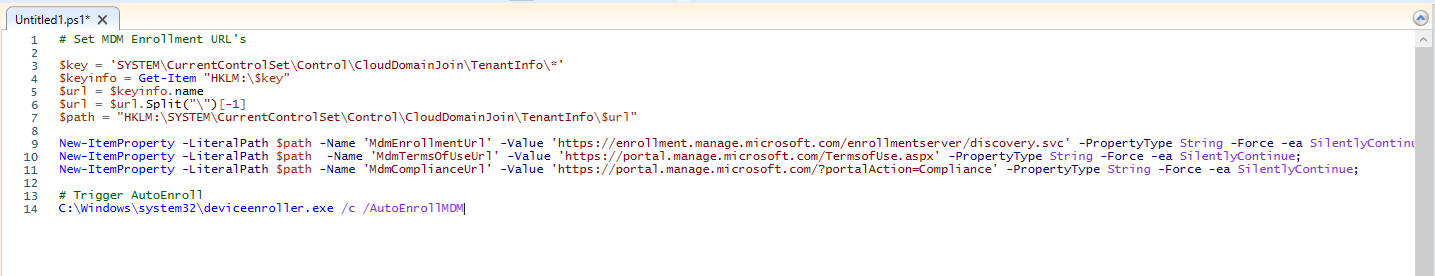
In this step we are going to trigger the enrollment with a PowerShell script. This method is extremely useful if you have installed an external RMM tool with which you can roll out PowerShell scripts. Please verify if your enrollment URLs are the same.
# Set MDM Enrollment URL's
$key = 'SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*'
$keyinfo = Get-Item "HKLM:\$key"
$url = $keyinfo.name
$url = $url.Split("\")[-1]
$path = "HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\$url"
New-ItemProperty -LiteralPath $path -Name 'MdmEnrollmentUrl' -Value 'https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmTermsOfUseUrl' -Value 'https://portal.manage.microsoft.com/TermsofUse.aspx' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmComplianceUrl' -Value 'https://portal.manage.microsoft.com/?portalAction=Compliance' -PropertyType String -Force -ea SilentlyContinue;
# Trigger AutoEnroll
C:\Windows\system32\deviceenroller.exe /c /AutoEnrollMDM
Run this script with Administrator rights and lean back. It can now take some time but your device should be enroll to Intune.
Option 2: Trigger the Enrollment with Sysinternal tools
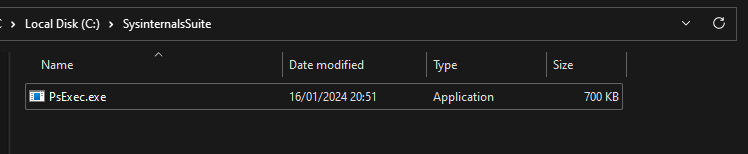
In this step we are going to trigger the enrollment with the Sysinternal tools. First of all download the Sysinternal tools from https://learn.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite. Extract the files and copy the PsExec.exe to the device you want to enroll to intune. I usually create a new folder on C:.
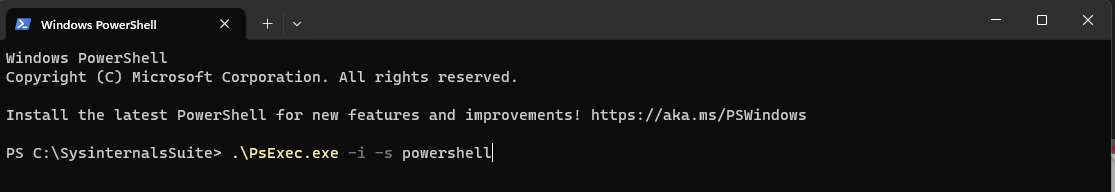
Now open a Windows PowerShell session and navigate to the saved PsExec.exe file. In my cas I would navigate to C:\SysinternalsSuite. Enter the following command.
.\PsExec.exe -i -s powershell
The device will now try to enroll to Microsoft Intune. This can take some time but should work.
Conclusion
You learned how to enroll existing Entra joined Devices to Microsoft Intune. We have discussed the Prerequisites and gave you two options to trigger the enrollment on the device. On the end we showed you where you can check the enrollment status on the device event viewer.
Did you enjoy this article? Dont forget to follow us and share this article. You may also like the the following articles.